Understanding the DevSecOps Pipeline for Software Security
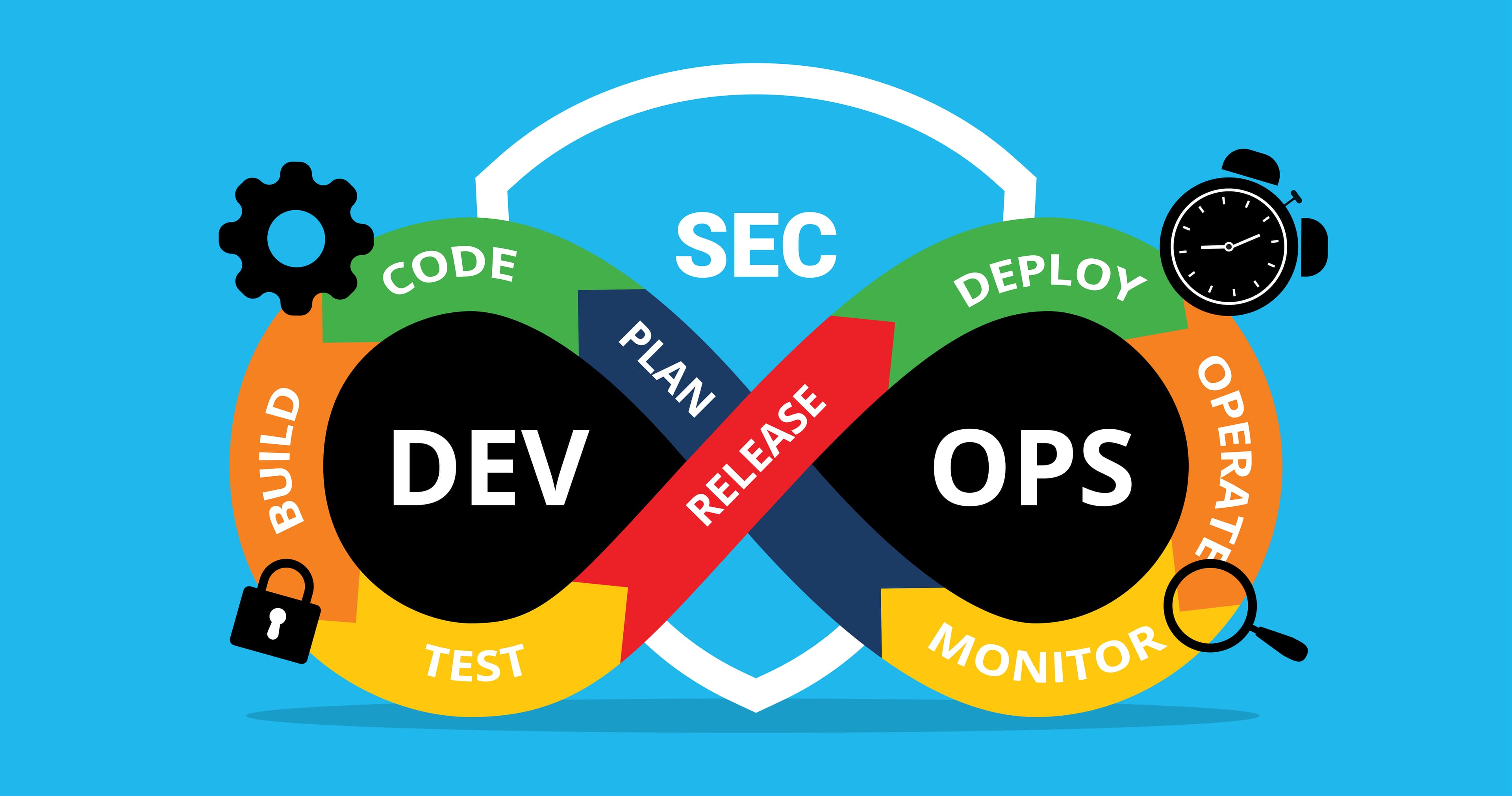
Security in the software development lifecycle is paramount, but balancing speed with security can be challenging. By implementing a DevSecOps pipeline, you can shift security left and build it into the process from the start. This allows vulnerabilities to be caught early and often, reducing risk.
In this article, we will explore the key components of a DevSecOps pipeline. You will learn how to leverage automation tools for security checkpoints, integrate vulnerability scanning and code analysis, and enable continuous monitoring.
With the right approach, you can deploy code quickly without compromising robust security standards. Read on to learn how a DevSecOps pipeline enables you to release secure, resilient software quickly.
What Is a DevSecOps Pipeline?
Imagine a pipeline where development, security, and operations work perfectly. This is the vision of a DevSecOps pipeline, an automated workflow that integrates these crucial practices into a single, efficient process.
Building upon the principles of CI/CD (Continuous Integration and Continuous Delivery), DevSecOps takes it a step further.
While CI/CD emphasizes rapid development and deployment, DevSecOps seamlessly integrates security checks and practices throughout the entire pipeline. This ensures vulnerabilities are identified and addressed early, minimizing risk and preventing costly delays down the line.
This approach is often called "shift left," where security becomes integral to every stage, from code development and testing to deployment and monitoring.
Instead of waiting for the final stages to check for security weaknesses, DevSecOps actively embeds security measures throughout the process.
This is the vision of a DevSecOps pipeline, an automated workflow that integrates these crucial practices into a single, efficient process.
Here's a breakdown of how this works:
Planning and Code Development: Secure coding practices, threat modeling, and vulnerability scanning become part of the development process, ensuring secure code.
Continuous Integration and Testing: Every code change triggers automated security scans, integrating with existing CI/CD pipelines for seamless testing and feedback.
Continuous Deployment and Monitoring: Security checks continue post-deployment, monitoring for vulnerabilities and potential threats in the production environment.
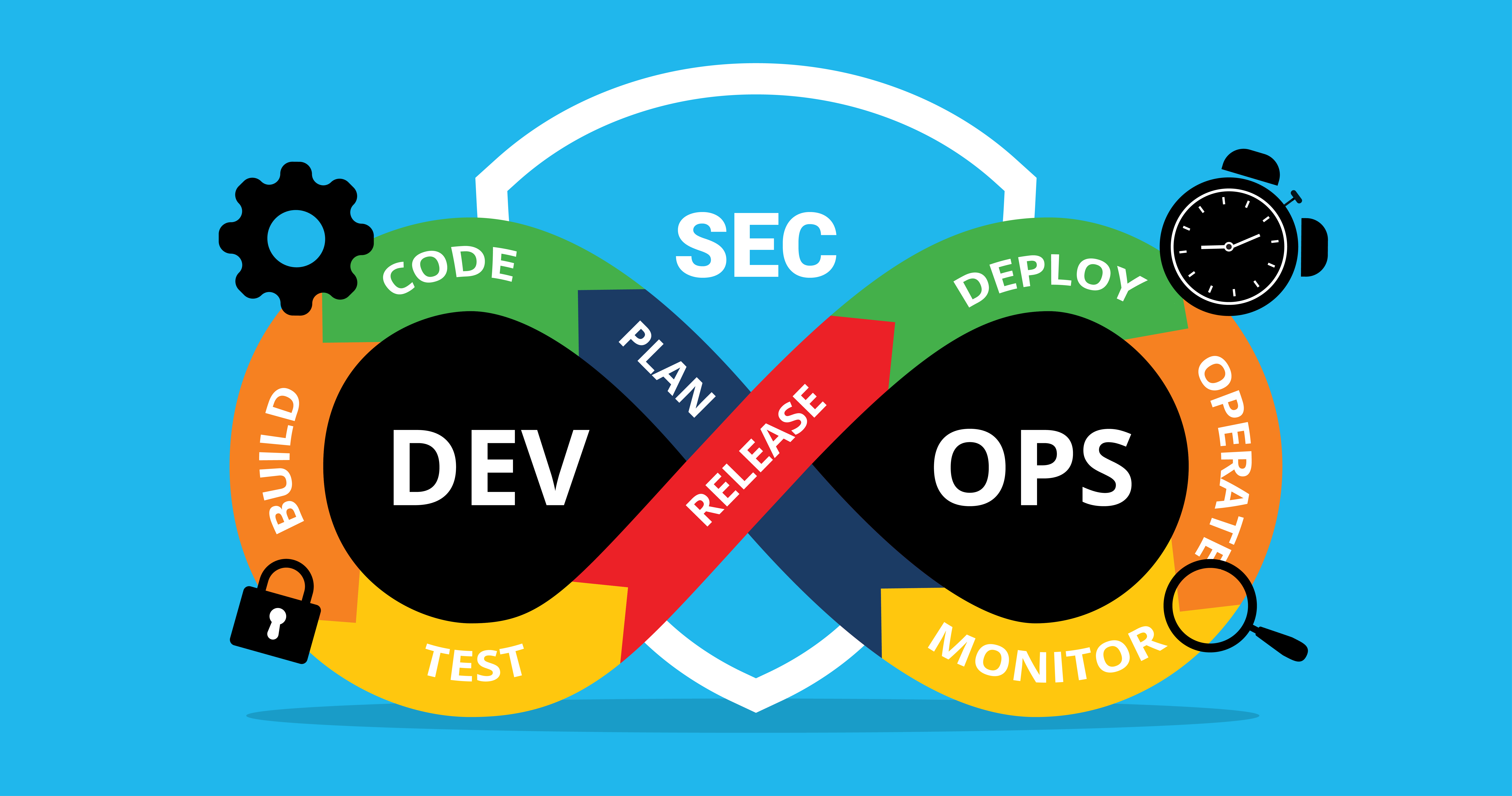
Key Security Checkpoints in the DevSecOps Pipeline
Planning and Threat Modeling
The first stage of the DevSecOps pipeline involves defining security requirements and identifying potential threats. Teams conduct threat modeling using frameworks like STRIDE to determine vulnerabilities. They can then implement controls to mitigate risks before coding begins.
Static Application Security Testing
Static application security testing (SAST) tools scan source code for vulnerabilities. They detect issues like SQL injections or cross-site scripting early on, allowing developers to remediate them quickly. SAST solutions provide security feedback directly within developers’ workflows, facilitating fast fixes.
Dynamic Application Security Testing
After building the application, dynamic application security testing (DAST) tools simulate attacks to uncover vulnerabilities. DAST solutions crawl the application, analyze requests and responses, and detect weaknesses like broken authentication or access control issues. They provide details on found vulnerabilities so developers can resolve them before deployment.
Continuous Monitoring
Even with extensive testing, new threats may emerge after deployment. Continuous monitoring tools actively scan the application in production, detecting anomalies and vulnerabilities in real time.
They alert security teams immediately, allowing for quick responses to potential incidents. Continuous monitoring is crucial for gaining visibility into the security posture of applications post-deployment.
The DevSecOps pipeline integrates security practices into development and delivery workflows using automation tools at each stage. It facilitates team collaboration, improves applications’ security, and enables faster, more secure software releases. Organizations seeking to strengthen their cybersecurity stance would benefit from implementing a robust DevSecOps pipeline.

Benefits of Using a DevSecOps Pipeline
The DevSecOps pipeline provides numerous benefits when implemented properly in an organization’s software development lifecycle (SDLC).
Improved Application Security
Integrating security practices early and continuously in the development process leads to enhanced protection of applications and systems.
The shift left approach of addressing security issues in the planning and development stages reduces vulnerabilities that could be exploited. Regular scanning, testing, and monitoring also help identify threats faster so they can be restored quickly.
Accelerated Release Cycles
Automating security procedures and making them a part of the pipeline improves the speed of development. Manual security testing and last-minute fixes before release are eliminated. Developers can release code faster without compromising on security. The collaboration between teams leads to fewer roadblocks and less rework.
Reduced Costs
Identifying and fixing security issues early significantly reduces costs associated with vulnerabilities discovered late in the SDLC. The financial impact of data breaches and system compromises is lowered. Resources are optimized since security is built in rather than added on at the end.
Improved Collaboration
DevSecOps fosters closer collaboration between development, operations, and security teams. Breaking down silos and encouraging shared responsibility for security leads to a more robust product. Collective ownership of risks and open communication at all stages create a supportive environment focused on a common goal.
Challenges and Considerations
Implementing DevSecOps practices requires overcoming several challenges within organizations and their development processes.
Cultural Shift
Transitioning from traditional development silos to collaborative DevSecOps teams necessitates a cultural shift. Developers, security professionals, and operations engineers must collaborate continuously, requiring open communication and a shared understanding of objectives.
This transformation of mindset and workflow is complex and takes time. However, by starting with small, iterative changes, teams can incrementally adopt DevSecOps principles.
Selecting and Integrating Tools
With the variety of security tools available, choosing the right mix for an organization’s needs poses a challenge. Teams must evaluate tools based on functionality, compatibility, and cost. The selected tools must be integrated at appropriate points in the development pipeline, requiring technical resources and expertise. Start with a basic set of tools, learn how they work together, and then expand from there.
Balancing Speed and Security
Teams strive to release new code and features in fast-paced development environments as quickly as possible. However, integrating security practices into the pipeline adds time to the overall process. Teams must focus on automation, prioritizing vulnerabilities, and keeping security lightweight when possible.
By anticipating and addressing these challenges, organizations can successfully implement DevSecOps pipelines. With improved security, enhanced collaboration, and faster releases, overcoming challenges is well worth it.
DevSecOps practices, when done right, ultimately save time and money, enabling teams to build secure software at the speed of business demands.

Achieving Continuous Monitoring and Feedback Loops
Use tools that scan for vulnerabilities and threats in real time to facilitate continuous monitoring of applications and incorporate feedback loops. Static Application Security Testing (SAST) and Dynamic Application Security Testing (DAST) tools should be leveraged to analyze source code and test running applications.
By integrating these tools into your CI/CD pipeline, you gain visibility into risks the moment code is committed, allowing issues to be addressed immediately.
Continuous monitoring also entails reviewing system logs, API calls, and user behavior regularly. By analyzing this data, anomalies can be detected, which may indicate an attack.
Defining key risk indicators (KRIs) and key performance indicators (KPIs) to determine normal vs abnormal behavior is critical. An alert should notify the appropriate teams to investigate if a KRI threshold is met.
To close the feedback loop, findings from monitoring activities should inform updates to security policies, standards, and tool configurations. For example, if a new vulnerability is discovered in a library, the pipeline can be adjusted to scan for that issue going forward. Monitoring data can also highlight areas where security awareness and education need to be improved.
Collaboration tools facilitate information sharing between DevSecOps team members. An integrated platform where all scan results, alerts, and notes are logged in a single place, visible to anyone concerned, helps break down silos. Teams can discuss issues, determine the best solutions, and work together to reverse risks promptly.
Continuous monitoring and feedback loops lead to a robust DevSecOps pipeline that adapts to changes and efficiently produces secure software.
With the right tools and collaboration, risks are identified and resolved rapidly, reduced vulnerabilities, and applications deployed securely.
Conclusion
As we conclude, the importance of implementing a robust DevSecOps pipeline is clear. By integrating security at multiple checkpoints throughout the development lifecycle, organizations can shift security left and build more secure software.
Using automation tools for vulnerability scanning, code analysis, and continuous monitoring enables development teams to catch issues early. While some upfront investment is required, the long-term benefits of reducing risk and minimizing costly breaches later make implementing a DevSecOps pipeline well worth the effort.
We hope this overview has provided valuable insights into how you can leverage DevSecOps to strengthen your software security. If you want to implement a DevSecOps pipeline, our software consultants can help you.
Contact us to learn how our company can benefit you and your business.